Ouch – Security gaffe exposes addresses of elite iPaders.
The full list of email addresses is floating around on the Internet :o
Tags: Apple, AT&T
Comments Off on iPad Users’ Email Addresses
Hacker pilfers browser GPS location via router attack
Even if it is a month late :)
Oh – and Happy New Year while I am posting :D
Tags: GPS
I read today that Manchester Airport has installed full body scanners to determine if users are carrying prohibited items. These scanners are developed by Rapiscan Systems, and the idea of them is that they will provide greater security for passengers, as well as improving their travelling experiences.
For more information about these scanners read Airport scanner shows ‘naked’ images or watch the video in ‘Naked’ scanner in airport trial.
Clearly such scanners will raise security concerns. Therefore, certain measures will be taken to protest users privacy:
- The operators will be in separate locations
- The operators will not be able to see the passengers’ faces
- The operators cannot use personal devices to capture images
- The images cannot be stored by the system
These measures are admirable, but I am not sure if they are really that useful.
Personally, I would not mind somebody seeing these images of my body, especially if it improves my airport experience!
However, I wonder will these scanners be used in other locations in the future, without knowledge or consent of the people being scanned. For example, such a scanner could be used at the entrance of a nightclub. Would this be a valid privacy concern?
Tags: Rapiscan Systems, UK
Comments Off on Naked Airport Scanners
I got my first Bank of Ireland phishing email last week, and I have got about three per day since! A typical one looks like this:
Subject: 365 Banking: You are required to confirm your email address
Date: Sun, 04 Oct 2009 20:50:23 +0200
From: Bank of Ireland <accounts@boi.ie>
To: xxx@xxx.xxx
http://www.sp-ad.com/.www.365online.ie/
The url looks really convincing, and I found it quite difficult to explain how to extract the domain name to some non-technical friends.
The page looks really convincing also! I did not visit it myself, but I used an online service to capture a screenshot of it:
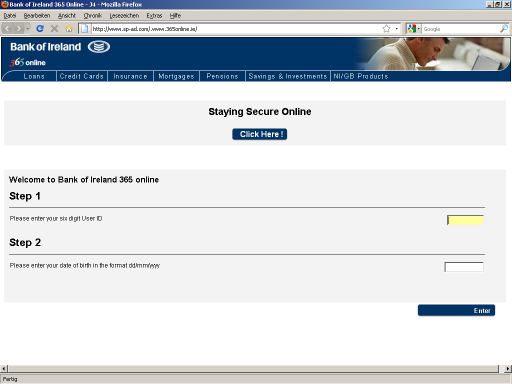
Bank of Ireland Phishing Screenshot
The real page can be viewed at https://www.365online.com/.
Tags: Bank of Ireland, Phishing
Comments Off on Bank of Ireland Phishing Emails
A friend recently sent me this interesting article – Super-safe Web browsing.
Comments Off on Super-Safe Web Browsing
There seem to be a lot of laptops being stolen this week in Ireland! See Inquiry after HSE laptops are stolen and Bord Gáis customer details on stolen laptops for details and video reports. The greatest concern in both of these cases is the sensitive data that might now be used maliciously. Hopefully, they were all stolen for the value of the hardware, and nothing more will come of this!
However, it does make me wonder how many more incidents like this will need to happen before companies decide to encrypt all data on all laptops! Apparently, I am not the only person wondering this! The main opposition political party in Ireland now wants to make encryption mandatory according to Mandatory encryption for laptops needed. In practice I do not think that this is very practical. For example, how strong must the encryption be? How must the keys be stored? Will the legislation try to cover these details?
Politicians trying to legislate technology :|
I also wonder if all of this data really needs to be stored locally on laptops!
I do not have any sensitive data on my laptop, and hence I do not use any encryption software. However, I have heard good things about TrueCrypt. It is open source, and available for all major operating systems.
Tags: Encryption, Ireland, TrueCrypt
Comments Off on Stolen Laptops
The Irish Government has finally decided to abandon the badly conceived eVoting system that it purchased several years ago!
Ireland uses a proportional representation system, and it is not uncommon for counting to take several days. Therefore, the eVoting system was intended to produce almost instant results. However, it was determined by an independent commission that the system did not provide a sufficiently secure and verifiable audit trial.
For more details about this story see Gormley scraps e-voting system, or the harshly written Ireland scraps evoting in favour of ‘stupid old pencils’.
I am delighted with this decision, because I think that the purchased eVoting system would have provided fewer verifiable audit facilities than the current paper based system. This is a pity, especially when you consider that a well specified system could have provided a significantly more verifiable audit trial. For example, every voter could have been supplied with a unique random identifier after he/she voted. The voter could then use this number online later to determine this his/her vote was correctly recorded, and contributed to the overall result.
Perhaps the best feature of the paper based voting system is that it provides very entertaining viewing :D
Tags: eVoting, Ireland
Comments Off on Irish Government Abandons eVoting
I tend to connect to the Internet a lot with my laptop in public places. I have no confidence in the security provided by Windows (2000 or XP), and I am am extremely sceptical of any software based firewalls for Windows. I am a firm beliver of hardware based security!
So I am very interested in some products by Yoggie that I saw recently. This video explains them:
In particular, I like the Gatekeeper Pro in inline mode. I think that this would be perfect for me if only it also included WiFi.
Tags: Firewall, Windows 2000, Windows XP, Yoggie
Comments Off on Yoggie Computer Security Solutions
You work in a large organisation that deals primarily with very sensitive information. You develop procedures to ensure that this sensitive information is handled correctly at all times. You invest in hardware solutions to ensure that your systems remain secure. You develop access control models that are based on biometric identification. You use the most secure protocols and algorithms to encrypt data. Indeed, you do everything that you can think of to ensure you have the strongest security possible.
Then some photographer in the right place, and at the right time, uses his digital camera and zoom lens to capture a photograph of a very sensitive document.
If you are not sure what I am referring to, then take a look at Police chief quits over blunder. It is actually a great example of why security requires an all encompassing multi-faceted approach.
Tags: UK
Comments Off on The Weakest Link in the Security Chain

